s embedded and machine to machine (M2M) devices evolve, new issues are rapidly emerging that affect both legacy systems and those being planned. Network security is one of those.
Malicious attacks on Supervisory Control and Data Acquisition (SCADA) and other industrial control and smart grid networks are a major concern. Recently the Industrial Control Systems Cyber Security team noted that there are now several new, publicly available exploit tools that specifically target Internet accessible industrial control system and programmable logic controllers (PLCs). Targeted systems include those from Rockwell Automation, GE, and Schneider Electric. And this is just the beginning of an evolving threat with malicious hacking to industrial espionage, and even cyber-terrorism.
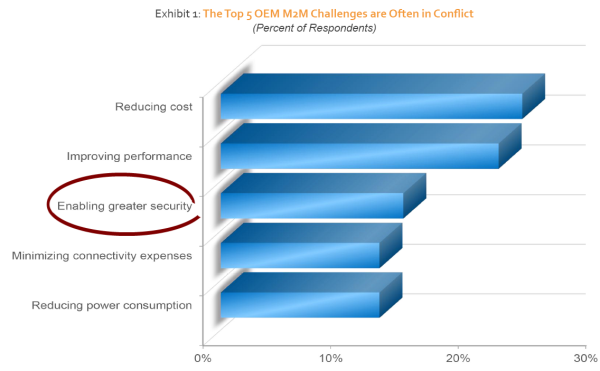
According to a new study from VDC Research security is the now the number three concern for M2M OEMs after cost and performance.
There is now an exposed soft underbelly in many deployed M2M systems that is vulnerable to hacking, denial of service (DoS) or other unwanted intrusion. Most of these systems were not designed to withstand the kinds of sophisticated cyber-attacks we are seeing today. According to VDC most engineers did not even considered security in their prior designs.
Even today embedded engineers are looking to add connectivity without factoring in the potential security risks. Many of these systems are home-grown and do not have the benefit of a commercial real-time operating system or proven security software.
Quadros Systems has been actively supplying security for M2M and embedded systems for many years. Our SSL/TLS package provides application level security to HTTP and FTP protocols. And our IPsec/Internet Key Exchange (IKE) package offers encryption security at the IP layer.
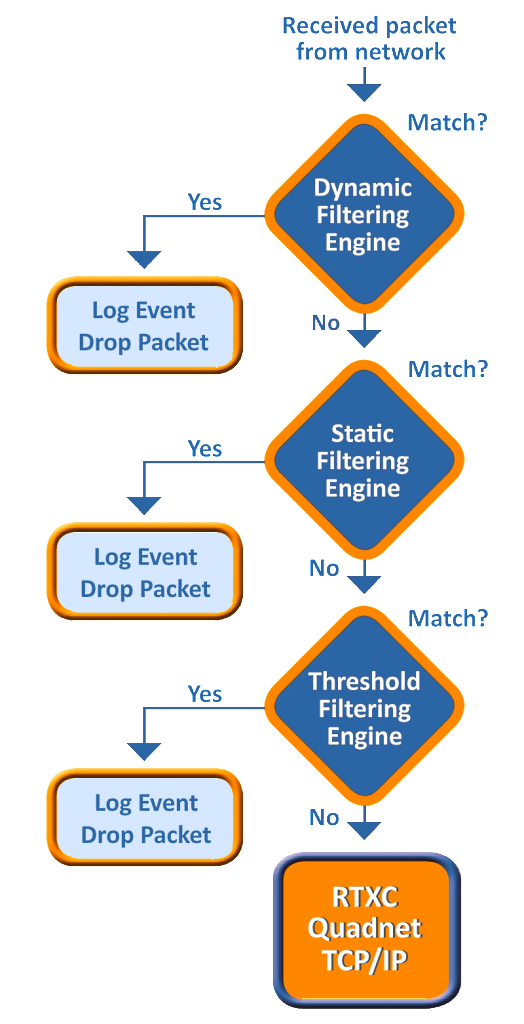
Last week we announced our most recent solution to address the network security: an embedded firewall. We have partnered with Icon Labs to offer three stage protection to customers using the RTXC Quadnet Ethernet-TCP/IP stack: static filtering, rules-based filtering and threshold filtering.
Floodgate Packet Filter has been used to provide security for industrial control applications, small footprint industrial firewall appliances and MCU based control devices. It provides Stateful Packet Inspection (SPI) and rules based filtering to protect embedded devices from real-world cyber-attacks. Rules-based filtering utilizes white-listing and black-listing to define system criteria such as port number, protocol, or source IP address for protection. Floodgate also features Stateful Packet Inspection (SPI) that provides dynamic packet filtering based on the state of the connection to a device.
The combined solution will add a layer of protection against threats such as packet floods, request storms, port scans, malformed IP packets and corrupted Ethernet frames. It is designed to meet ANSI/ISA/IEC/TS 62443 standards for cyber security. The system is designed explicitly for use in embedded devices with limited memory and processor speeds that require secure network implementation certified to standards such as the ISASP 99 which is measured by the Wurldtech Achilles® Test Platform.
Get more details on network security options from Quadros Systems:
Application Security (SSL/TLS)